Secure Your Nginx Server in 2024: Achieving an A+ Rating on Qualys SSL Labs
Ensure the security of your Nginx server with these comprehensive best practices for TLS configuration. By following these steps, you can earn an A+ rating on Qualys SSL Labs and protect your website from potential threats in the coming year.
Jan 2nd, 2024 by Nicolas Béguier
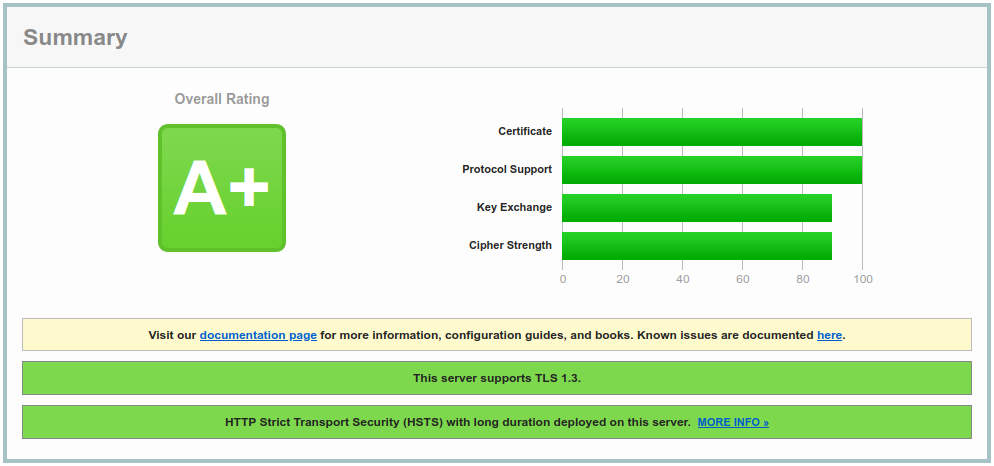
One objective can be to have a grade of A+ on Qualys SSL Labs.
1. Basic security
# Only return Nginx in server header
server_tokens off;
Using TLS 1.2 and TLS 1.3 on an nginx server is important because these versions of the TLS protocol provide stronger security features and improved performance compared to older versions. Some of the key benefits of using TLS 1.2 and TLS 1.3 include:
- Stronger encryption: TLS 1.2 and TLS 1.3 use stronger encryption algorithms and key lengths to protect data transmitted over the internet.
- Improved performance: TLS 1.2 and TLS 1.3 are designed to be more efficient than older versions of the TLS protocol, which can result in faster connection times and improved overall performance.
- Improved security: TLS 1.2 and TLS 1.3 include additional security features, such as Perfect Forward Secrecy, which helps to prevent an attacker from using previously recorded traffic to decrypt current traffic.
Overall, using TLS 1.2 and TLS 1.3 helps to protect the confidentiality, integrity, and availability of data transmitted over the internet, and it is an important security measure for any server that handles sensitive information.
ssl_protocols TLSv1.2 TLSv1.3;2. Cipher Suite
There are four main types of encryption algorithms:- Key exchange
- Authentication
- Block encryption
- Message Authentication
Some of these algorithms, such as RC4, DH, 3DES, and EXP, should be avoided due to their lower levels of security. It is important to prioritize the use of more secure algorithms in order to balance security with accessibility for customers.
For more information on the security of different cipher suites, you can refer to the following link: https://ciphersuite.info/
# Compilation of the top cipher suites 2024
# https://ssl-config.mozilla.org/#server=nginx
ssl_ciphers ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:DHE-RSA-CHACHA20-POLY1305;
3. Optimization
The "ssl_prefer_server_ciphers" directive tells the server to use its own list of preferred ciphers, rather than relying on the client to specify them.
# Perfect Forward Secrecy(PFS) is frequently compromised without thisssl_prefer_server_ciphers on;
The "ssl_session_tickets" directive is used to disable the use of SSL session tickets, which are used to resume SSL sessions and improve performance.
ssl_session_tickets off;The "ssl_session_timeout" and "ssl_session_cache" directives enable SSL session caching, which helps to improve performance by allowing the server to reuse previously established SSL sessions.
# Enable SSL session caching for improved performancessl_session_timeout 1d;
ssl_session_cache shared:SSL:10m;
The "ssl_buffer_size" directive sets the size of the buffer used for sending data over SSL.
# By default, the buffer size is 16k, which corresponds to minimal overhead when sending big responses.# To minimize Time To First Byte it may be beneficial to use smaller values
ssl_buffer_size 8k;
The "ssl_stapling" and "ssl_stapling_verify" directives enable OCSP (Online Certificate Status Protocol) stapling, which is a method of checking the revocation status of SSL certificates without the need for a separate request to the certificate authority. This helps to improve performance by reducing the number of requests that need to be made.
# OCSP staplingssl_stapling on;
ssl_stapling_verify on;
4. Security headers
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft, to site defacement, to malware distribution. This CSP configuration is highly secure, but it is recommended to test it first to ensure that it does not block third party scripts. CSP Evaluator is an excellent tool for testing your CSP configuration.
The HTTP Strict-Transport-Security response header (often abbreviated as HSTS) informs browsers that the site should only be accessed using HTTPS, and that any future attempts to access it using HTTP should automatically be converted to HTTPS.
# Security headers
## X-Content-Type-Options: avoid MIME type sniffing
add_header X-Content-Type-Options nosniff;
## Content-Security-Policy (CSP): Yes
## No 'script-src' directive, you need to test it yourself
add_header Content-Security-Policy "object-src 'none'; base-uri 'none'; require-trusted-types-for 'script'; frame-ancestors 'self';";
## The safest CSP, only block your website to be inside an inframe
add_header Content-Security-Policy "frame-ancestors 'self';";
## Strict Transport Security (HSTS): Yes
add_header Strict-Transport-Security "max-age=31536000; includeSubdomains; preload";
5. DH Param
Diffie-Hellman (DH) is a cryptographic algorithm used to establish a shared secret between two parties. It's commonly used in various cryptographic protocols to ensure secure communications over an untrusted network, such as the internet. DH parameters, often simply termed "DH params", play an essential role in this process.
It's crucial for security reasons that these parameters are generated in a strong and robust manner. Specifically, the size of the DH group (measured in bits) directly influences the strength of the cryptographic operation. Modern best practices recommend using a 4096-bit DH group for most applications.
To generate a 4096-bits DH group using the OpenSSL toolkit, you can use the following command:
# Generate 4096-bits DH groupopenssl dhparam -out /etc/ssl/certs/dhparam.pem 4096
After generating the DH parameters, you might want to inspect or verify them. To check the content and details of the generated DH group, use
openssl dh -in /etc/ssl/certs/dhparam.pem -textOnce you've generated the DH params, you need to integrate them into your server configuration to use them. For servers running Nginx, the directive is `ssl_dhparam`. Here's how you can specify the path to the DH params in the server configuration:
ssl_dhparam /etc/ssl/certs/dhparam.pem;Complete configuration
GitHub GIST LinkConclusion
Evaluate your configuration using the following link: https://www.ssllabs.com/ssltest/analyze.html